

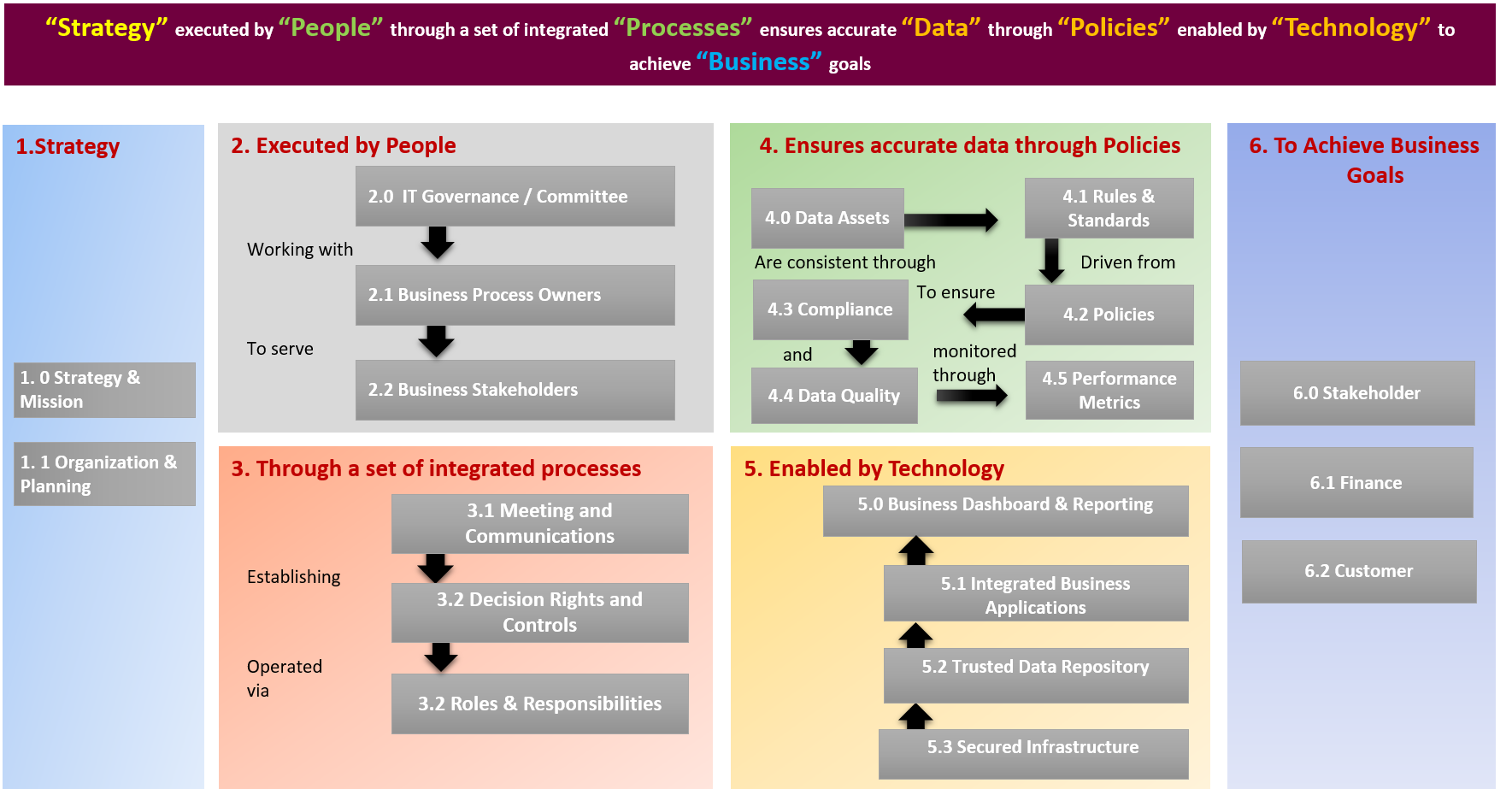
Legacy Modernisation
Legacy Modernization is the continued process of transforming Legacy Systems in order to reduce IT environment complexity and costs, increase data consistency, enable collaboration across platforms and improve process flexibility. It mostly aims at transforming existing systems into web based thin client systems and integrate multiple related systems. One of the major challenges in legacy modernization is to ensure that the modernized system has similar capabilities with compatibility with existing data formats.
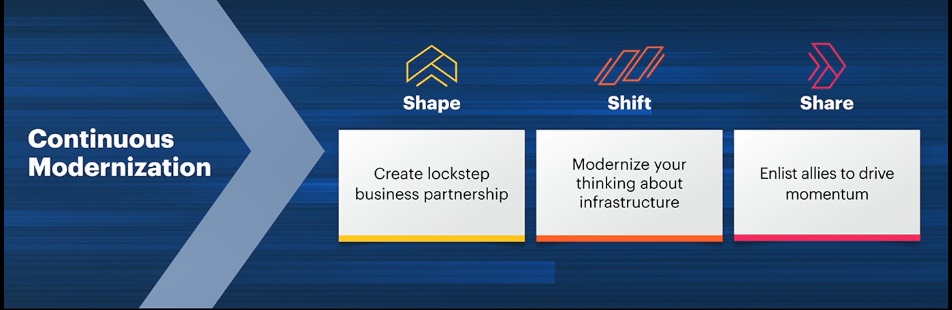
Continuous Modernisation
The first and most obvious option for organisations is to rewrite their existing software. Regular rewrites are continuous modernisation. Some organisations underestimate how long and expensive developing software can be or overestimate the longevity of a new application.One way costs can be reduced and longevity extended is migration, such as moving local, legacy systems to the cloud.
Operating Model
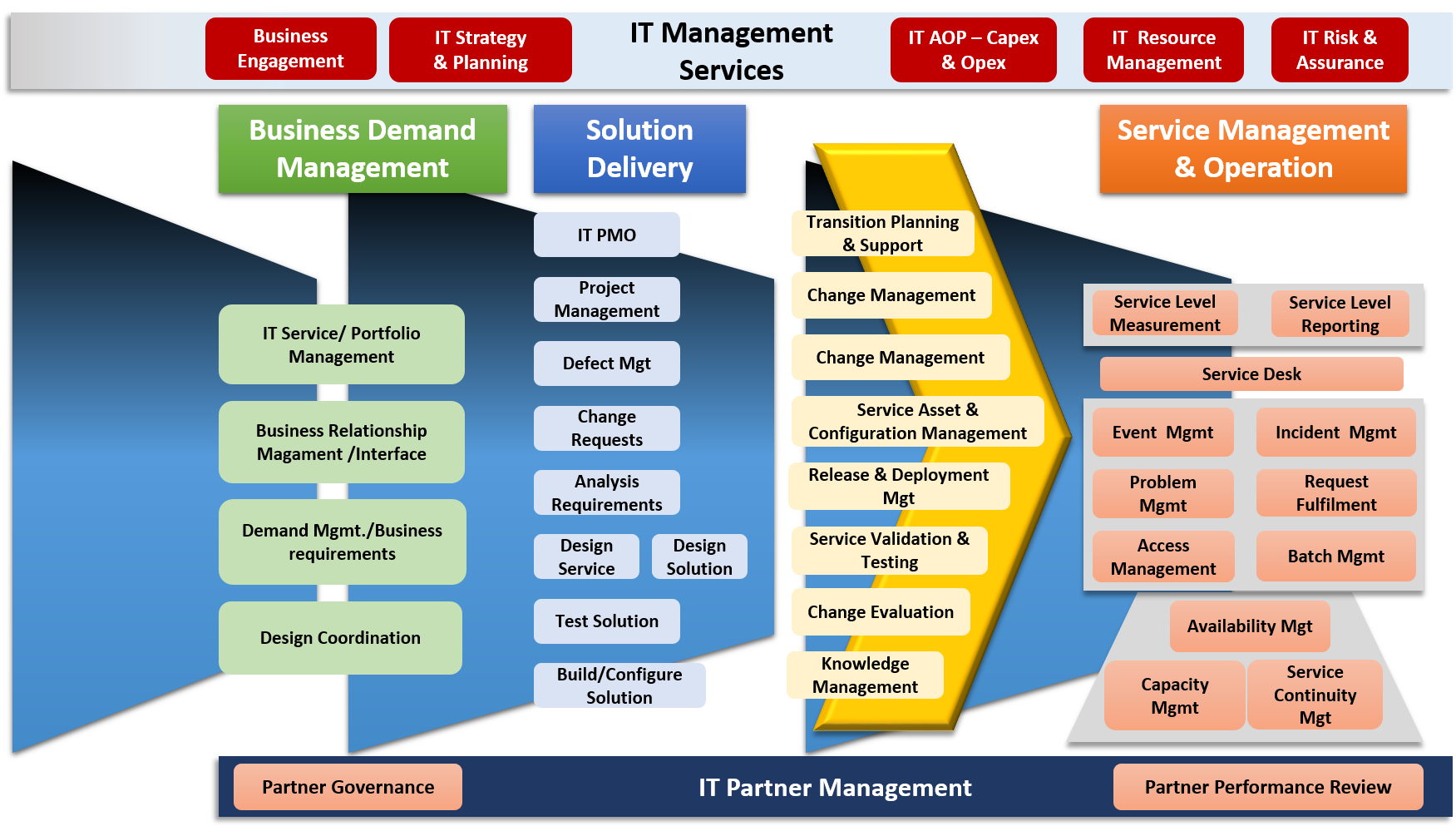
We Follow Proven Integrated LEAN and ITIL Practices
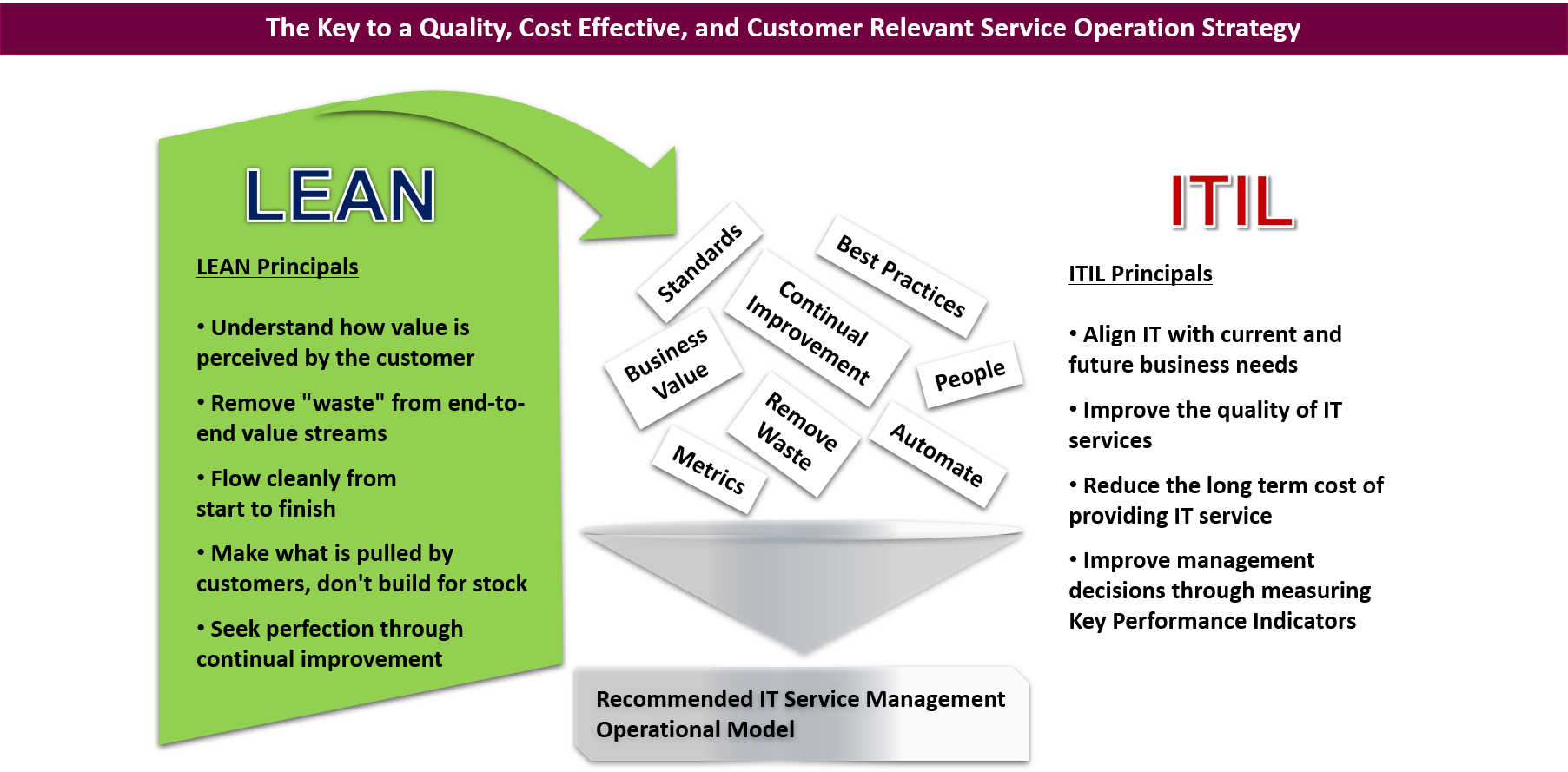
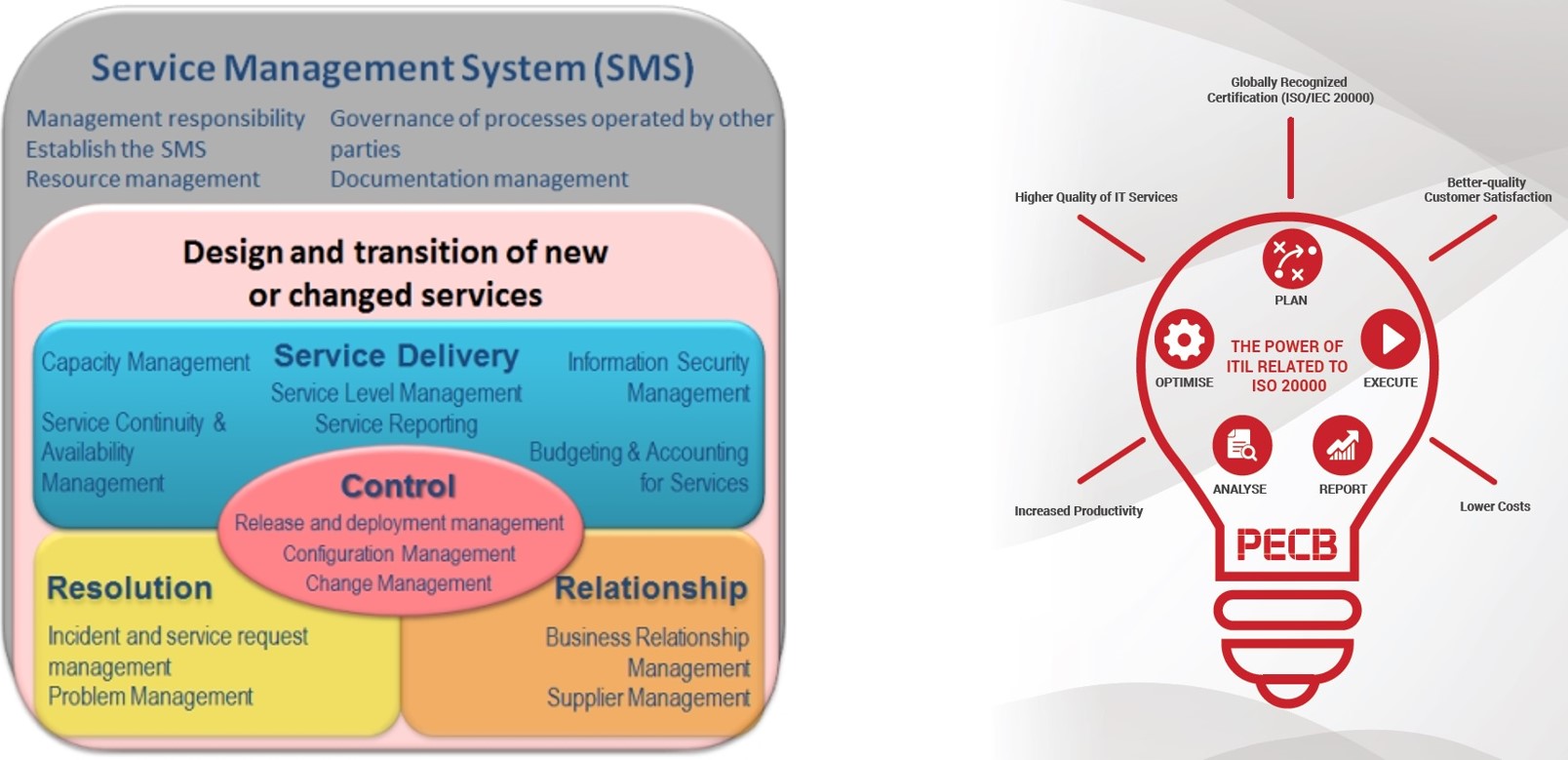
ITIL Process Maturity Assessment Model
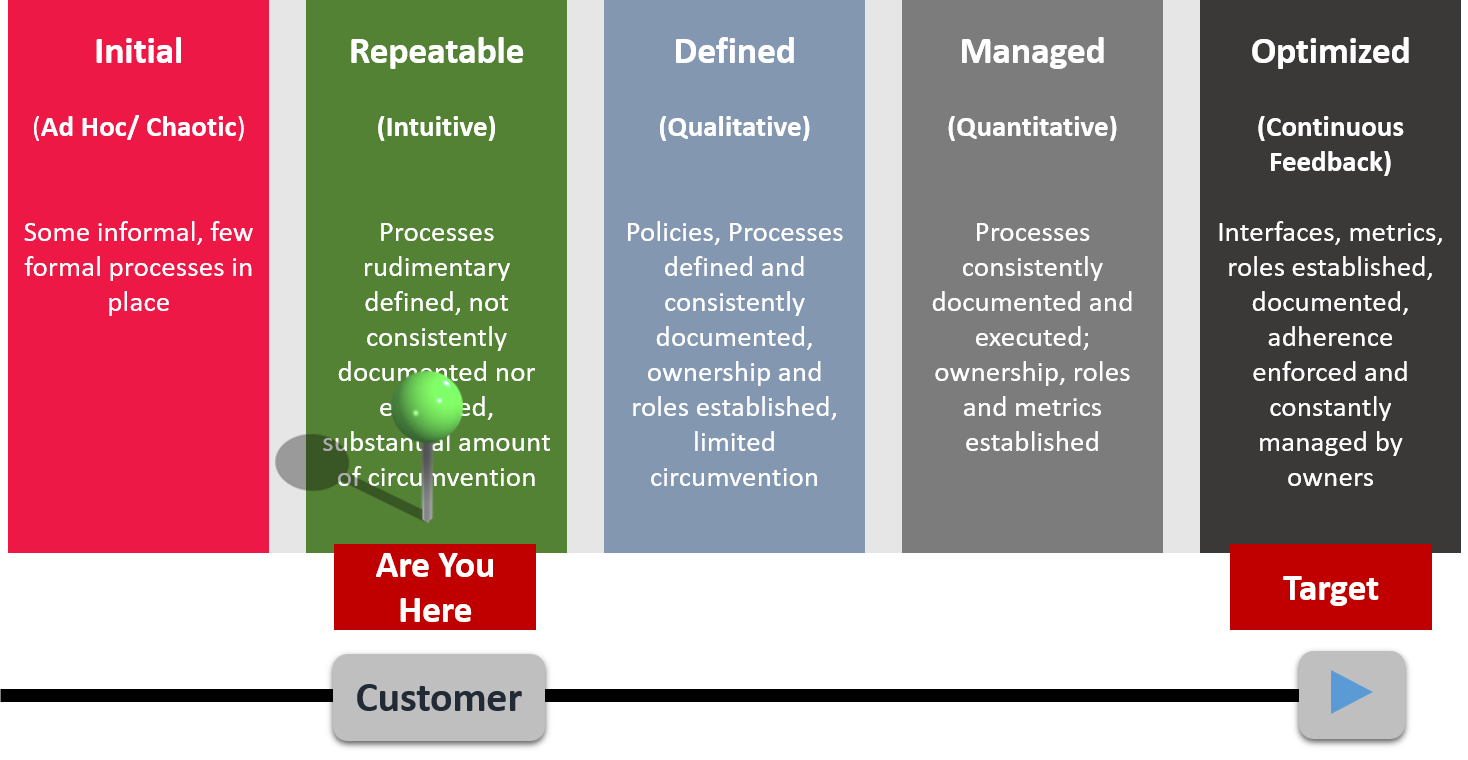
Implementation Approach : ITIL Based

Digital product managers
Digital product managers oversee the development of a new online product, from its inception to its launch. Using market data, they manage existing products, and identify ways to enhance those products based on public perception.
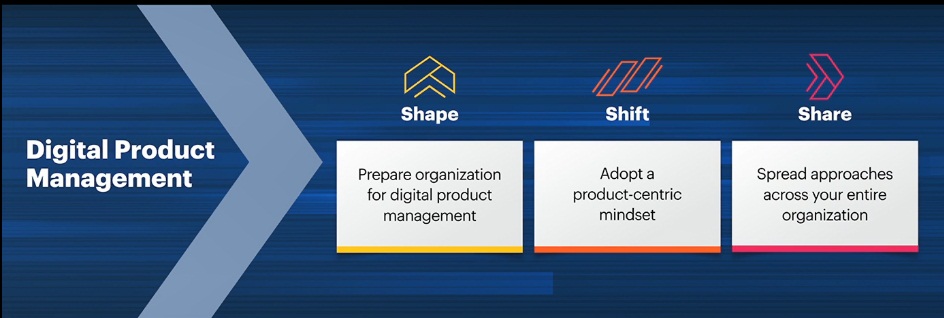
Digital Product Management
- Creating product roadmaps
- Taking products from initial concept through user research, co-creation, and rapid prototyping
- Agile and lean management practices for creating software and digital products
- Social media and market testing methods
- Applying perspective from best practices in platform based strategies.
End to End Security around Information
- Security Policy
- Organization of information security
- Asset Management
- Human Resources Security
- Physical and Environmental Security
- Communications and operations management
- Access Control
- Information Systems Acquisition
- Development and Maintenance
- Information Security Incident Management
- Business Continuity Management
- Regulatory Compliance
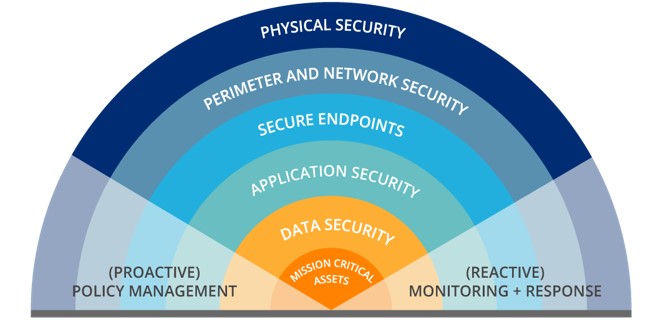
Increase IT Security Using Machine Learning

With the advancement and variety of cyber threats, IT staff’s efforts to detect, evaluate, and remediate suspicious codes and events grows every day
To streamline this process, Machine Learning technology optimizes security products, helping automate the detection of potential vulnerabilities and attacks, enabling behavioral analysis tied to security monitoring of corporate infrastructures
Evaluate data quality, Save Time Explore more of your team’s skills
ISO 27001 Framework
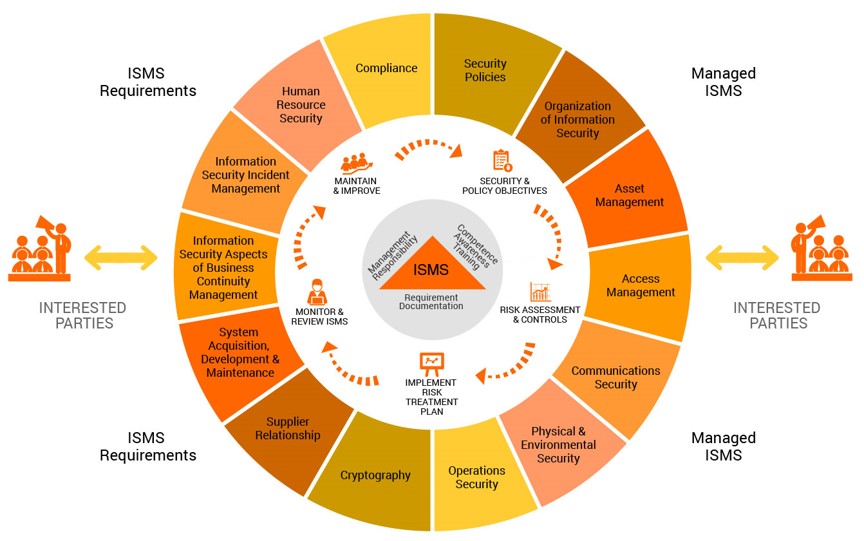
ISO/IEC 20000 Related To ITIL Model
IT Security Training: Our Offerings



